Organizations increasingly depend on computer networks, cloud computing, and data to run their enterprises. As a result, they need to continuously identify and mitigate loopholes within these shared networks that attackers can exploit.
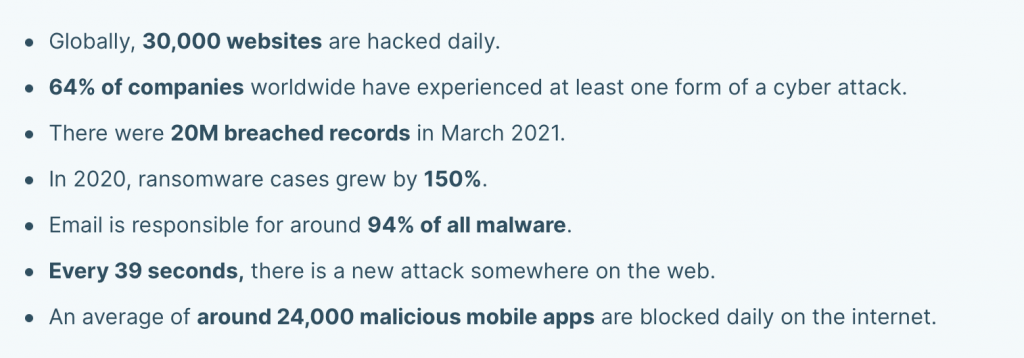
On any given day, cybercriminals hack into 30,000 websites globally, while 64% of businesses worldwide experience some form of cyber attack. Such alarming statistics are the reason why companies require thorough and continual vulnerability scanning to safeguard the company’s networks.
A vulnerability scan is an excellent tool for identifying potential weaknesses within your system that attackers might exploit. In addition to pinpointing security loopholes, system scanning helps measure the effectiveness of your security programs in preventing actual attacks.
Below, we’ve developed a guideline to help you conduct effective system vulnerability scanning that yields measurable results.
What is Vulnerability Scanning?
Vulnerability scanning is the proactive process of discovering network, device, and application weaknesses that attackers can exploit for malicious intent. Another way to define it is an automated test that identifies network loopholes to predict potential attacks and develop appropriate countermeasures.
How does a scan work? IT administrators use software to inspect your networks, servers, devices, and applications. The software identifies loopholes by comparing the findings against a list of common threats, defects, bad actors to ascertain their risk level.
Why is Vulnerability Scanning Necessary?
New vulnerabilities and security threats manifest daily, and without frequent system assessments, attackers can easily exploit your company’s weaknesses. Additionally, customer-facing applications contain valuable information that can be exploited for financial gain.
Scanning establishes repeatable procedures that quickly identify vulnerabilities before attackers get a hold of them for exploitation.
Furthermore, it helps in meeting regulatory standards that require companies to protect transactions and minimize vulnerabilities.
Certain IoT devices and computing equipment do not get regular patch updates because they’re low-cost or do not meet the minimum requirements for a security update.
In such a case, running vulnerability scans will help you identify devices that do not get regular security updates so you can decommission them. A scan will also help you disconnect such devices when their underlying security software expires.
Lastly, some devices such as printers do not automatically update their security patches. However, they’ve still considered an attack surface because they connect to your private network and expose passwords, sensitive documents, and IP addresses. You’d need to examine and update their security features manually. Vulnerability scanning allows you to secure printing ports, update the firewall, and monitor network printing.
Vulnerability Scanning vs Penetration Testing
Vulnerability scanning and penetration testing are often mistaken to be the same concept. However, both approaches are different in terms of scope and tools used.
While a vulnerability scan is an automated test that discovers potential vulnerabilities, penetration testing involves actual personnel examining systems through specific manuals to test the strength of your security programs.
Additionally, penetration testing simulates cybercriminals through ethical hacking, research, and exploiting vulnerabilities identified through a scan. From the comparison above, you can tell that penetration testing is far more detailed and comprehensive than a vulnerability scan.
But a vulnerability scan is equally crucial because it’s the first step to providing critical information on security gaps within your system. So both tests need to go hand-in-hand for you to get accurate results and improve the strength of your security solutions.
The key similarities between vulnerability scans and penetration testing are:
- Both tests are designed to improve and optimize IT security systems
- They are both a compulsory requirement according to government data security standards
- They both use software to perform tests and discover vulnerabilities

Vulnerability Scan Types
There are five types of vulnerability scans categorized according to the forms of IT assets they analyze. They include:
1. Credentialed Vulnerability Scan
A credentialed scan utilizes administrator privileges and user credentials to deep scan a network and uncovers hidden vulnerabilities. In addition, this type of scan uses credentials to log in to host devices to query local hosts on whether they’ve applied security patches to the vulnerabilities identified. Credentialed scans also help in probing for client-side software vulnerabilities and allows for customized security solutions.
Also known as an authenticated vulnerability scan, this type of scan determines the strength of a given network by allowing full access to system configurations and thorough testing of each device.
2. External Vulnerability Scan
An external scan is typically conducted outside of the system—the scan targets perimeter defenses such as network and device firewalls. Additionally, eternal assessments track platforms such as your web applications, websites, and public IP addresses. This type of scan detects weaknesses in external-facing networks that are easily discoverable by potential attackers.
3. Active Vulnerability Scan
Active vulnerability scans work by deploying data packets into a network to query specific endpoints. By sending test traffic into individual endpoints, testers analyze IP addresses, device names, firmware versions, and patch levels to identify vulnerabilities. The major problem with active scanning is that it does not monitor a network 24/7, so hidden threats can bypass the scan and infiltrate your system.
4. Continuous Vulnerability Scanning
Also known as passive scanning, continuous vulnerability scanning silently monitors a network without disrupting normal operations. Passive scanning works more effectively than active scans because it identifies vulnerabilities in real-time without interrupting regular network activity. This gives a realistic view of potential gaps and simplifies remediation.
5. Unauthenticated Scan
An authenticated scan explores network defects without logging into the system. Also known as traditional or non-credentialed scans, this method scans host protocols, servers, and ports without network privileges to identify misconfigurations that can be exploited.
A non-credentialed scan is ideal for large networks with traditional structures. This scan can also perform brute force assessments for credentials to identify their strength in keeping away authorized access.
Benefits of Vulnerability Scanning
Scanning your networks and mitigating security risks is essential for a safe and secure operating environment. Below are several vulnerability scanning benefits:
Vulnerability Scanning Helps Organizations Stay Ahead of Cybercriminals
Cybercriminals continuously scan the web for vulnerabilities to exploits on any given day. This means that any successful attacks are mainly due to vulnerabilities that were found and exposed.
That is why scanning your assets regularly is highly effective in protecting your company from cyber-attacks. It’s also a cost-effective approach because identifying weaknesses early enough is less costly than recovering from an actual attacker.
Enables Compliance to Security Standards
Though the government does not directly regulate specific vulnerability issues, they expect organizations to protect user data shared among their networks. Regular scanning ensures your organization complies with data security standards such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS).
Improves the Effectiveness of Security Solutions
Many factors contribute to a secure environment, but vulnerability scanning ensures companies apply accurate solutions to specific issues. Without proper scanning, you may end up using blanket services that do not effectively deal with security defects. You may also end up with expensive security services that do not meet your expectations.
Increases the Visibility into your IT Environment
Modern visibility scanners provide a unified console that collects inventories of your IT assets so they can perform effective vulnerability scans. This centralization gives administrators proper records of their assets and can easily re-purchase devices. Visibility also helps in keeping track of user activity to identify malicious traffic.
Vulnerability Scanning – Challenges
In as much as a scanning has numerous benefits, there are a few challenges. They are:
Timely Resolution of Vulnerabilities
It’s one thing to identify vulnerabilities, and it’s another to implement resolutions quickly. The time it takes to close up loopholes could prevent or allow attackers entry into your systems even if you successfully identified the vulnerability. In addition, this works against organizations that have many bureaucracies and require extensive approvals for change implementation.
Infrequent Vulnerability Scanning
Scanning should be frequent for it to yield effective results. However, most organizations conduct infrequent scans without a formal routine or lack the resources to establish routine vulnerability scanning. This infrequency ends up delivering sub-optimal findings that do not significantly improve the overall security setup.
Additionally, infrequent scans may end up piling up security loopholes creating a large backlog of issues not resolved. This backlog may overwhelm the security team, who may not have the time or resources to deal with a huge backlog of vulnerabilities effectively.
Lack of a Prioritization Plan
Companies face multiple vulnerabilities, and to effectively handle all of them, teams need to prioritize loopholes according to risk and threat levels. Additionally, poor prioritization exposes the company to higher risks because of focusing on low-risk vulnerabilities.
How CG Technologies can help
CG Technologies understands the challenges small and medium-sized companies face when trying to keep one step ahead of potential cyber attackers. We offer a range of managed security services designed to identify potential security vulnerabilities and prevent your business from ransomware attacks or a data breach. If you would like to discuss your security concerns with one of our experts, contact us before the unthinkable happens to your business.
