Phishing is a form of cybercrime that applies deception to steal personal or business information from unsuspecting users. Email phishing scams are the most popular tactics that attackers use to steal confidential data for harmful purposes. Furthermore, phishing emails are the leading tools that attackers use to carry out scam activities.
A recent FBI report from their Internet Crime Complaint Center indicates phishing as the leading scam method, with 241,342 complaints received in 2020. Furthermore, email compromise led to combined losses of $1.8 billion.
Such statistics prove that phishing email awareness is critical to protect employees and businesses from becoming victims of a phishing email attack. Below, we examine what phishing entails with clear phishing email examples. You’ll also learn about the best practices to protect your business, employee, and customer interests.
What is Phishing Email?
A phishing email is a form of social engineering where scammers impersonate people and legitimate organizations through email, adverts, and text messages to gain trust and steal confidential information. These attackers steal personal and financial data through social engineering psychology and technical subterfuge.
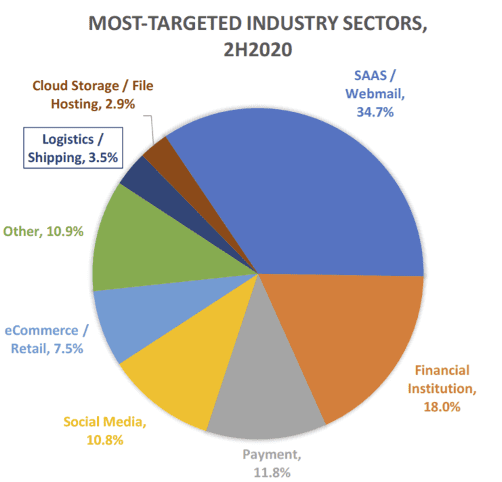
The word ‘phishing” is coined from the term “fishing” because criminals lure unsuspecting users with “bait” so they can provide sensitive information such as passwords, credit cards, and account numbers. In most cases, the bait is a catchy, familiar, or valid-looking email with a link that leads you to a fraudulent website where you provide your personal information. What is a phishing email? Social engineering attacks are commonly delivered via email because users tend to trust email communication that looks legitimate hence why webmail (Gmail, yahoo-mail, hot-mail) were the most targeted platforms in 2020.
How Does Phishing Email Work?
Phishing awareness involves training your stakeholders how to detect phishing emails and how to protect their personal information. So how does a phishing email work?
The common denominator in phishing attacks is social networking. As more social and business networks collect background information, attackers scan the internet to collect personal data to develop phishing strategies. Attackers collect information from social media sites such as personal interests, home addresses, work history, and even their friends’ data. Their goal is to make the phishing attempt look as legitimate as possible to trick unsuspecting users.
Once the attacker develops a believable phishing tactic, they send an email or text message that appears legitimate to the victim. This message typically contains a malicious link or attachment with the intent to collect personal data, web history, saved passwords, or install the malware in the victim’s device.
Attackers carry out their malicious strategies through harmful links embedded in emails or texts, malware, or harmful attachments. Typically, these are the actions they want you to perform when they send you to receive the message:
- Click and download an attachment
- Reset your password – this prompts you to provide your current passwords
- Respond to a social media request
- Log in to a new wi-fi network
- Enable macros for a Word document
- Fill a form with personal information and click submit
There are three forms of phishing attacks. The actions above apply to the phishing tactics below:
- Spear phishing: attackers target specific organizations or individuals with techniques that reference something familiar to the victim. For example, their co-worker, their supervisor, location, or email addresses.
- Pharming: pharming applies DNS poisoning to redirect victims from an authentic website to a fake one. The purpose is to trick users into logging into the fraudulent website with their credentials, steal this information and take control of their system.
- Voice phishing: this is a form of phishing where scammers steal information from voice-based tools. Scammers apply speech software to hack into a users’ home telephone or mobile device to leave fake voicemails that notify them of suspicious bank or credit card activity. The goal is to push the user to call back and divulge personal information.
Phishing Email Examples
These real-world phishing email examples will give you a clear picture of the message’s structure so you can better detect a potential attack. The common phishing emails that attackers use include:
1. Emails Sent from a Public Domain
Legitimate organizations do not send messages through public domain emails like @gmail.com or @hotmail.com. Legitimate emails, even from Google, come as a private domain, typically prefixed with the company’s name, e.g. @google.com.
Sometimes attackers can try to mimic private domains to look authentic. In such cases, confirm the email’s legitimacy by Googling the address or confirm by getting in touch with the actual company before acting on the potentially fraudulent email.
Also, check the source email address by hovering with your mouse over it. For example, finance@paypal.com VS finance@paypal23.com may look the same to an unsuspecting user.
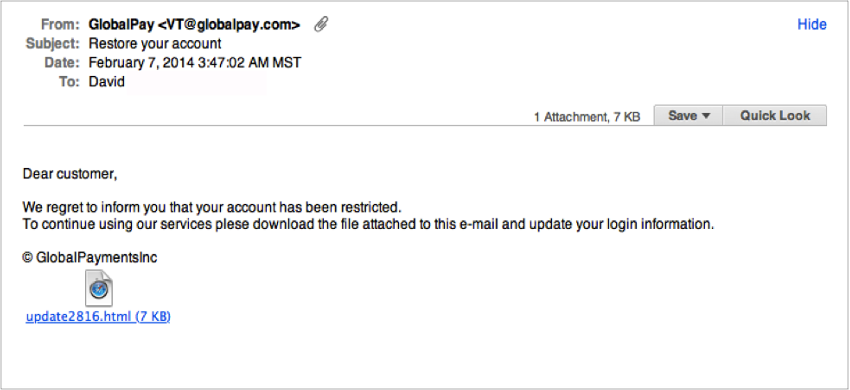
2. Emails Requesting Personal Information
Legitimate companies do not request personal data or financial information via email.
Attackers using this method will either provide a link or an attachment for you to submit confidential information. The example below looks legitimate because the attackers mimicked a private domain. The catch is in them asking for sensitive information.
1. Tech Support Phishing Emails
These phishing email examples are also quite popular because everyone’s using technology in one form or another. Tech support phishing scams often claim to provide support from legitimate organizations like your internet provider. They place a toll-free number for users to call to receive further assistance. The attacker’s goal is to install and activate remote access software to the victim’s device when they call the fake toll-free number.
Sample Phishing Email
In this section, we’ll break down the anatomy of a scam email to help you identify a potential attack:
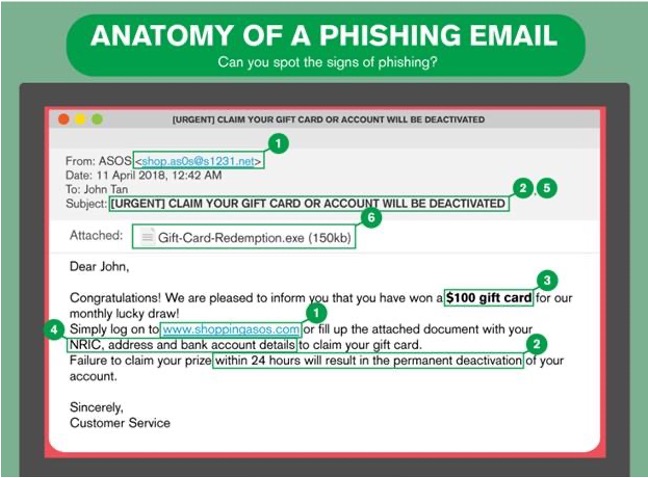
The email above highlights the typical structure of a phishing email. It may not look sophisticated but contains the top markers in most phishing emails:
- No. 1 is the suspicious sender’s address and link that’s not from the legitimate organization. If in doubt, Google the correct address or notify their customer care to validate the link.
- No 2 and 5 express an urgency to try and get you to act quickly. A legitimate business does not force customers to take immediate action. If it’s something urgent, they’ll word it professionally or give you a call.
- No. 3 and 4 are the “bait”. Scammers know people love free goodies. Inserting the promise of a gift card easily piques curiosity and drives users to click the link in no. 1 or download the attachment in no. 6.
How to Protect against Phishing Email?
Now that you have a detailed understanding of phishing, you’re better off preventing any potential phishing attacks before they happen. There are three primary strategies for how to protect your email from phishing:
- Install secure email gateways for your company inbound and outbound emails. This gateway scans emails for phishing, spam, and malware. The software also blocks harmful content, so it does not reach the user.
- Implement Post Delivery Protection within your network to detect any malicious content that may bypass the security gateways. Some attackers develop sophisticated phishing techniques that can slip through tight security measures. It’s essential to add an extra layer of protection.
- Train your stakeholders on how to identify phishing attempts and how to stop getting phishing emails. Human action is always required in any malicious attack. Therefore, routine training equips your employees, vendors, managers, and directors with the skills to identify and report any suspicious activity.
How Managed Cybersecurity Sevices Help Protect your Business
Cybercriminals are continually developing new and ever more complex ways to get what they want. And, keeping up with the latest threats and protecting against them can be a full-time challenge for busy IT staff. Our managed cybersecurity services take care of your IT security needs while you focus on your business’ growth. Our services and solutions are designed to address the problems and obstacles that face small to medium businesses every day.
Our managed services for cybersecurity include:
- Intrusion prevention technology that goes beyond a firewall
- Web filtering to prevent access to malicious and risky websites
- Pro-active threat analysis
- Best-of-breed antivirus protection
- Tools to prevent spam emails
- Email Phishing training for your staff
Our cybersecurity consulting services can keep you safe and secure and allow you to focus on what matters most, your business. Contact us to discuss your cybersecurity needs.
