Endpoint management is the systematic practice of discovering, deploying, updating, and troubleshooting endpoint devices in an organization. This practice hinges on endpoint software tools that ensure all systems in a company run smoothly and with minimal downtime.
With endpoint management, organizations supervise and authenticate accesses for all their devices, applications, and users to mitigate security threats. Consequently, effective threat mitigation is achieved through endpoint patch management, ensuring that all endpoints consistently have the latest security configurations.
Universal endpoint management (UEM) is another essential principle in endpoint management. UEM ensures all devices and users are centrally managed through a singular interface to improve resource utilization.
Enrolling endpoints into patch management and universal endpoint management practices protects your company’s IT landscape from unpredictable disruptions that can cripple operations.
Below, we explore endpoint management and what features to look for in an effective endpoint management solution.
What is Endpoint Management?
Endpoint management monitors, provisions, updates, and troubleshoots all devices connected to your organization’s network. Therefore, it’s not surprising that most cybercriminals target company endpoints. Given such a high probability for attacks, endpoint management is critical to a business’s success and even survival.
We’ve witnessed how security compromises have crippled successful businesses and cost them millions of dollars in lost revenue, reputational damage and fines. Endpoint management ensures company safety by providing all IT assets visibility and identifying potential loopholes for attackers to exploit.
Getting a good grasp of endpoint management helps organizations develop effective strategies to combat IT landscapes’ existing and unknown risks.
The underlying principle in endpoint management is security. This involves managing authentication and access rights to devices. This control measure involves:
- Restricting network access to authorized users and devices
- Tracking and monitoring endpoint access to identify malicious activity
- Applying endpoint security measures across your company’s IT landscape
- Developing a centralized interface for administrators to manage endpoints
Additionally, an effective endpoint solution enables automatic discovery and incident resolution leading to reduced incident remediation time and lowers maintenance costs. This way, you get to monitor company-wide IT components from a single console such as disk space, CPU, memory, event logs, hardware and software performance, etc.
Today, endpoint management extends to next-generation technology such as virtualization, cloud computing, IoT, and robotics. These technologies employ non-traditional computing through mobile-enabled operating systems and networks. In such instances, admins gain control over virtual environments to monitor, secure and control access to cloud infrastructure.
Enterprises accomplish effective endpoint management by applying software solutions that discover, visualize and manage all devices within their IT landscape. This is why it’s a recommended solution to help IT admins resolve incidents faster and optimize resources for a longer lifespan.

What is an Endpoint?
An endpoint is any internet-capable system that remotely sends and receives information through the network it’s connected to. Endpoints typically constitute of:
- Laptops
- Point of Sale systems
- servers
- Smartphones
- Desktop computers
- IoT devices
- Tablets
- Printers
- Virtual machines
- Cloud infrastructure
- Workstations
An endpoint represents attack entry points for malicious actors. Cybercriminals release harmful code into these endpoints to exploit system vulnerabilities to steal business data, personal information, or financial resources.
What is not considered an endpoint? It’s easy to classify all company devices as endpoints, but that’s not the case. These devices are commonly known as Customer Premise Equipment (CPE). CPEs include firewalls, switches, network gateways and are not endpoints because they’re a networking medium that allows endpoints to communicate.
Importance of Endpoint Management
The IT landscape has dramatically evolved in just under one year due to the COVID-19 crisis. The pandemic accelerated digital transformation across all sectors, and the old way of working is no longer practical. The workplace and business playground all revolve around interconnected on-premise and cloud infrastructure.
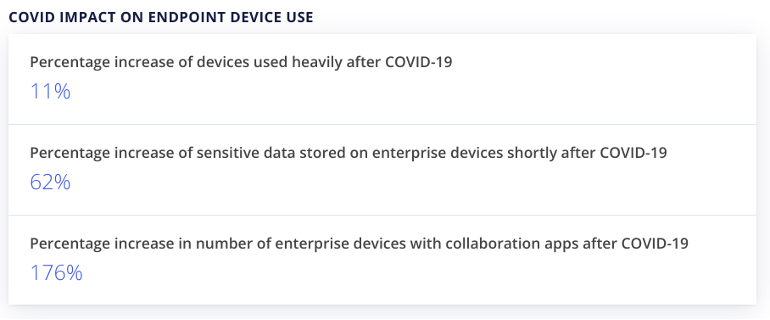
This heightened connectivity requires a strategic and agile approach to security because business data and personal information are at stake. Data is growing at unprecedented levels with no signs of stopping, so implementing advanced endpoint protection to mitigate potential risks is the best strategy. Below are some compelling reasons why endpoint management is critical to your business’s success:
1. Supports and Secures a Remote Workforce
As companies increasingly adopt remote work routines, endpoint management policies kick into gear to support the new workplace. Procedures such as Mobile Information Management and Mobile
Threat Defense ensures maximum security for work devices even when they’re off-premises.
These advanced endpoint protection software deliver updates and patches on a well-mobilized schedule to remote employee devices.
Additionally, cloud infrastructure simplifies system diagnosis and maintenance without straining the company’s private network. Such capabilities enable secure content access and distribution by simply requiring employees to have a stable internet connection.
2. Maintains Visibility Over All Your Endpoints
IT admins cannot control endpoints effectively without clear visibility on all their components. An endpoint interface gives front-line access to all IT assets for easier onboarding, software updating, and system configuration. Without clear visibility, admins may end up neglecting parts of your IT landscape resulting in poor resource utilization.
3. Application Management
Endpoint management allows IT professionals to install and manage business application features from a central console. You can integrate business apps and third-party software such as your email suite, ERP software, and web conferencing applications into your endpoint solution.
From here, you quickly deploy configurations, patches, updates, and bulk-purchase app features for end-users.
App management within endpoint solutions allows you to control who downloads business apps by turning permissions on and off. This practice prevents users from installing unauthorized apps into your company’s private network.
4. Identity and Access Management
As mentioned above, endpoint management lets you control devices and their security configurations. Furthermore, endpoint software provides various options for managing user identity and authorizations in terms of identity management.
For example, endpoint platforms allow you to deploy passcode settings and enforce authentication requirements when onboarding users to new devices. If the user does not comply with passcode requirements, the endpoint software notifies users to update their credentials accordingly.
When you need to decommission company devices, you can wipe out user credentials and identity details from the endpoint console.
5. Endpoint Device Management
Endpoint device management provides tools to secure company data by controlling access to work accounts when using personal mobile devices. The CG technologies endpoint management platform supports Android, iPads, and iPhones.
Admins can remotely lock devices if it’s compromised or stolen; you can wipe the user’s data and monitor device activity to track company data usage.
As an admin, you can manage which desktop computers or laptops have access to your data and see whenever users sign into your network. This capability allows you to monitor network activity and prevent breaches from harmful actors.
6. Endpoint Vulnerability Management
Endpoint vulnerability management orchestrates tools and practices for continuous threat management across company systems. This process involves discovering, assessing, reporting, and resolving vulnerabilities before they escalate into catastrophes.
Risks of Choosing the Wrong Endpoint Management System
Choosing the wrong endpoint management solution can incubate hidden problems and turn them into devastating issues. It would help if you had a solution that delivers accurate IT landscape reports to make data-driven business decisions.
Furthermore, if the software does not provide effective endpoint threat management, your organization may overlook potential vulnerabilities and be caught off guard when they eventually blow up.
Below are the significant downsides to choosing the wrong endpoint solutions

1. Reduced Operational Efficiency
The core objective of any endpoint management system is to support the business and improve efficiency. If the software does not deliver tangible results to the company, you may want to replace your endpoint management solution.
While measuring operational efficiency, some metrics to consider are fewer tickets, reduced help desk calls, shorter time to market for products, and more.
Increase security incidents and breaches – this is characterized by increased cases of malware infecting your devices, data loss, fewer patch releases, and infrequent backup cycles. Your endpoint solution should automatically improve security defenses by notifying admins of system breaches and deploying patches immediately.
2. No Reduction in Maintenance Costs
A good endpoint management tool helps organizations reduce costs by better optimizing resources. An excellent place to measure cost management is by checking your total cost of Ownership for hardware, licenses, cloud infrastructure, and third-party software.
If an endpoint management solution works efficiently, you can stretch these IT resources to deliver more value for the same subscription. So you’ll have better utilization of existing resources and fewer repurchases of software and hardware.
A suitable endpoint solution also helps minimize overhead costs due to a lesser need for office space and utilities.
Start Your Endpoint Management Solutions with CG Technologies
Business success now relies on how your IT landscape operates and delivers results. With state-of-the-art endpoint software, you automate all your routine IT tasks while improving the security of your valuable assets.
CG Technologies understands the expert resources and associated costs required to manage and provide endpoint security 24 x 7 can be overwhelming for any small/medium business.
We offer endpoint management security solutions to manage and protect your devices, including:
- Endpoint monitoring to identify and block risky devices
- Automated deployment of all security and anti-virus patches
- Endpoint security monitoring to identify and fix vulnerabilities
- Endpoint detection and response (EDR) services provide advanced protection against attacks
Our endpoint security service uses enterprise-level anti-virus solutions and endpoint security software to keep your business safe and secure, 24 × 7 × 365. Contact us to learn more about our hosted infrastructure services.
